Managed Cybersecurity Services for Small Business
Protect your business with managed cybersecurity services, zero trust security, MFA,
ransomware protection & secure Wi-Fi. Real security for the real world.
Managed Cybersecurity services Beyond Basic Antivirus Protection
24/7 Monitoring & Oversight
24x7x365 SOC
Compliance Reporting
Web & Threat Intelligence
Forcepoint database-backed web filtering
Patch & Application Control
Ivanti OS & third-party patching.
WatchGuard Zero-Trust Application Security
Device Encryption
Microsoft BitLocker key management
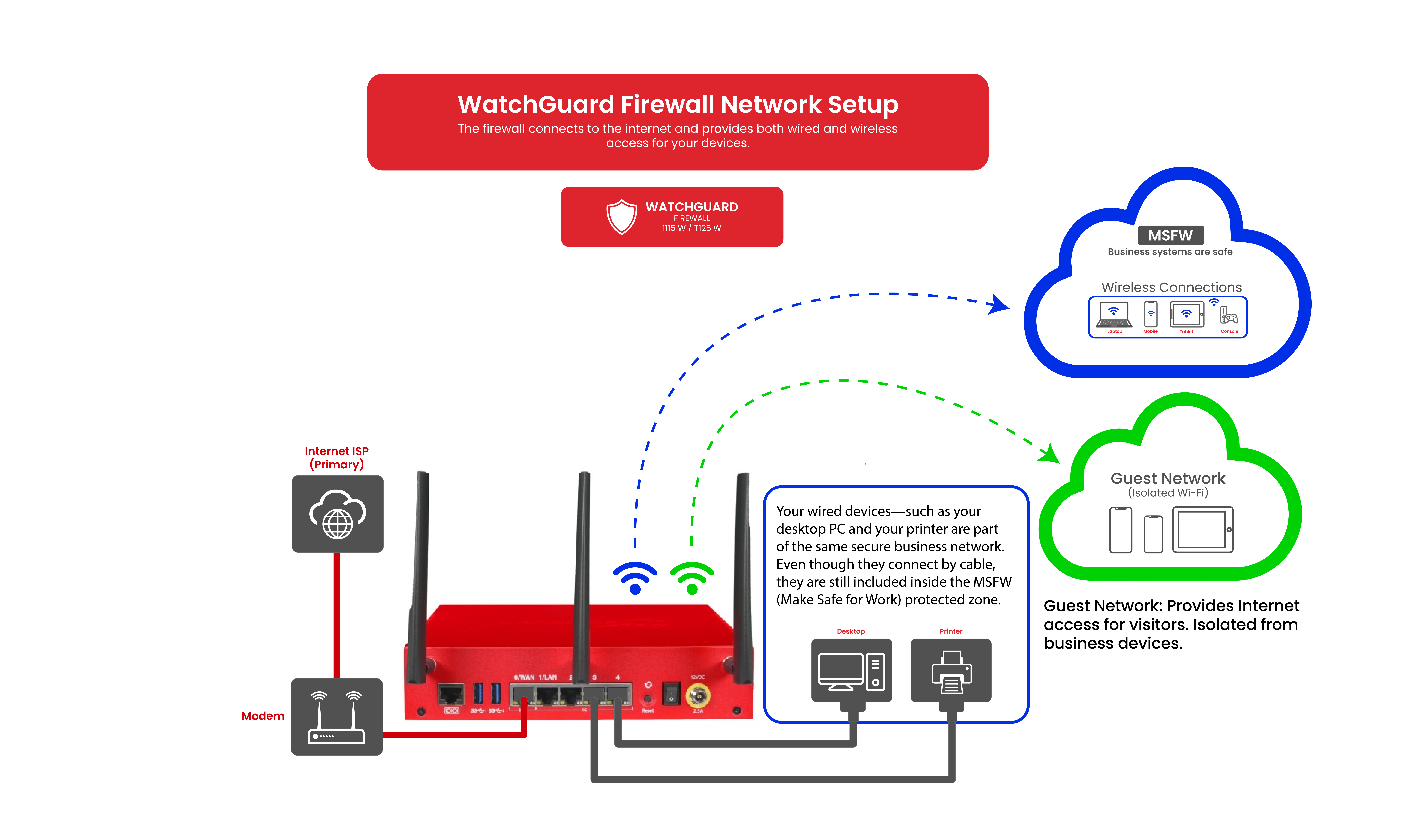
MSFW – Made Safe For Work
MSFW is Varpath’s blended cybersecurity solution designed to keep modern workplaces secure, compliant, and productive.
It brings together zero-trust security, intelligent content filtering, automated patching, and real-time threat protection into a single, managed approach. MSFW ensures employees can work safely without unnecessary friction whether they’re in the office or remote.
Zero-Trust by Default
Only trusted applications and behaviors are allowed to run.
Safe Browsing & Content Control
Intelligent filtering blocks risky, inappropriate, and malicious content.
Always Up to Date
Automated patching and encryption keep systems protected without manual effort.
Built for Business Compliance
Supports security and compliance standards without added complexity.
Emergency Services
Instant Protection When You Need It Most
Made Safe For Work + Paranoid Ruleset
Take security to the next level with our advanced paranoid ruleset. This build includes everything in the standard package, plus much stricter geo-blocking.
- Malware filtering with enterprise-grade protection
- Block almost all countries outside the USA
- Allow only essential global connections to keep the internet functional
- Enhanced network lockdown for ultra-secure environments
Made Safe For Work
Protect your business instantly with our preconfigured “Made Safe For Work” security package. This build is designed to safeguard everyday users with the most common protection needs.
- Zero Trust application security
- OS patch management (Mac + Windows)
- Application patch management (Adobe → Zoom)
- Block access to TOR endpoints
- Malware filtering to stop malicious threats
- Block access to high-risk countries (China, Russia, North Korea, etc.)
- Restrict access to gambling and adult content
- Intelligent filtering for a secure, work-ready environment
- Fast setup, get protected immediately
Add-ons:
- Encryption (WatchGuard Full Encryption add-on)
- 24x7x365 SOC (Security Operations Center) services powered by human security analysts supplemented by AI.
System Inventory & Risk Analysis
Not for distressed or actively attacked systems. This package provides a complete overview of your system’s current health and risks.
- Comprehensive system inventory & security assessment
- Identify vulnerabilities and risks across your network
- Expert recommendations for strengthening your defenses
- Option to migrate findings into a custom or preconfigured security build
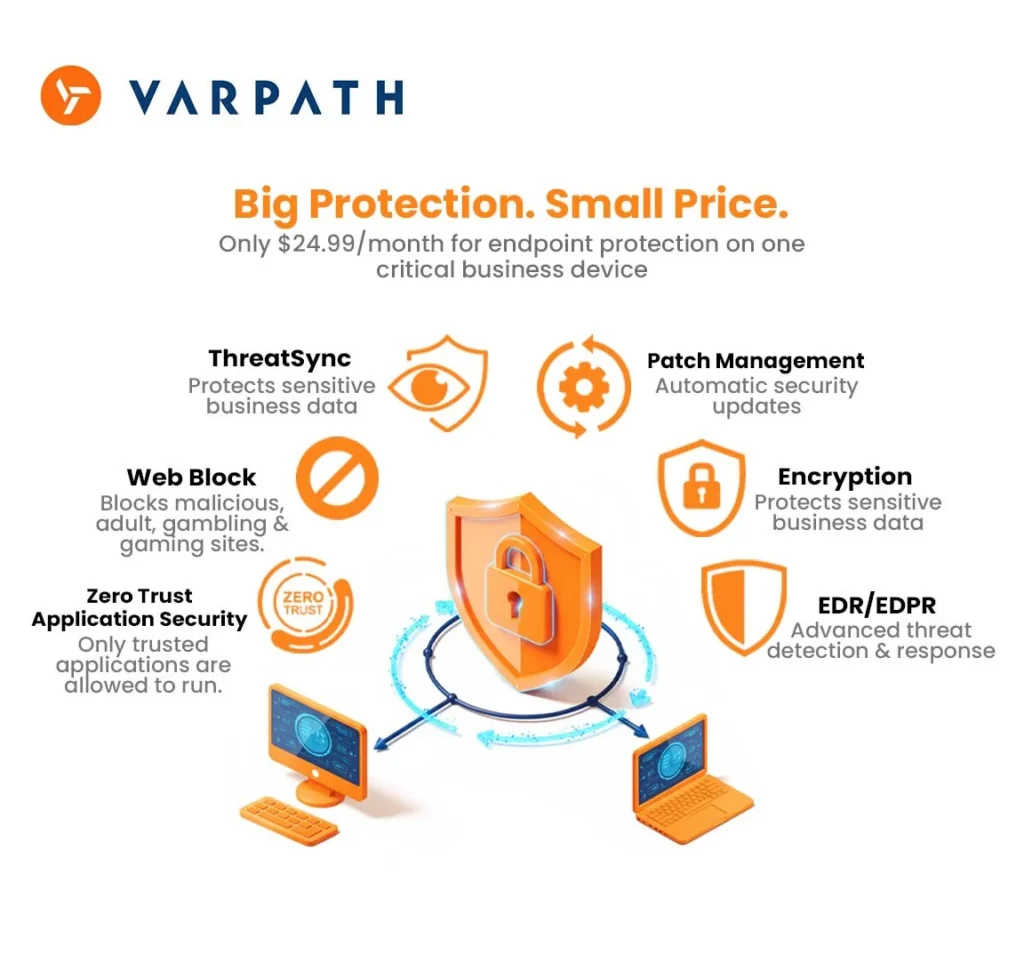
Managed protection for one Critical device
If your business depends on a single workstation, laptop or billing system, protecting it isn’t optional. When that one device goes down, work stops, revenue stalls and recovery becomes costly. Varpath delivers affordable, business-grade endpoint protection built specifically for small businesses that need reliability without enterprise complexity.
Built for businesses that can’t afford downtime.
Managed Cybersecurity Services
Get Started With Our Managed Cybersecurity Services

Secure Desktop
Fully cybersecurity managed secure Windows environment powered by WatchGuard and Varpath. Easy deployment, no hardware required.

Secure MFA
Cloud-based multi-factor authentication managed by Varpath. Easy API integration for your business apps.
Recommended Solution
Our All-in-One Security Bundle brings together everything your business needs to stay protected, connected, and efficient. Instead of managing multiple products separately, you get everything in one unified platform designed to work seamlessly together.
Ultimate Security Bundle
The all-in-one cybersecurity managed solution for small businesses to stay secure, compliant, and worry-free.
- Next-Gen Firewall → Blocks advanced threats & secures your network.
- Wi-Fi Access Point → Fast, reliable, and secure connectivity.
- Identity Protection → Prevents stolen logins with advanced authentication.
- Endpoint Security → Defends devices from malware & ransomware.
- Licenses, services, software & support included.
- Professional install

THE VARPATH WAY
We understand our clients have businesses to run. There is nothing for Varpath to protect if we don’t give you the freedom to profitably and efficiently run your business.
That’s why we take more than just a Zero Trust approach. We couple Zero Trust with a structure that is built specifically for small- and medium-size-businesses. An approach built over the last 15 years that relies on personal touch and efficient solutions. And, often most important to our clients, a respect for their privacy and freedom from restrictive policies.
Say goodbye to FUD. No more fear, uncertainty and doubt.

Real Security for the Real World
With Varpath, you get essential cybersecurity managed services, tailored to your operations, backed by unwavering support, and built on a financial model designed for your success.
Precise &
Powerful Security
Everything you need and nothing you don’t. Trust our experts to choose only the most effective technology to keep your security up to date, and avoid the overly complex, low impact clutter.
A Perfect
Operational Fit
We conform and scale to you, rather than asking you to adapt to us. Pick from sophisticated tools or easy AI based services for security that feels tailormade for your needs.
People
That Show Up
You don’t only hear from us when we need something. We get to know you and your business, engage at every level, and, we answer the phone when you need support. We care about building real partnerships and prove it every day.
Proven
Business Value
For businesses of every size to have powerful security, the price must be right! You want security solutions based on WatchGuard to be a top value even with MSP operations and services factored in… and that’s what we deliver.
Managed Cybersecurity Solutions
WatchGuard-powered managed cybersecurity services from Varpath.
Zero Trust Security
Application Zero Trust. A complete inventory and vigilant auditor of any and all applications installed.
Multi Factor Authentication
Secure logins with AuthPoint MFA protect employee and customer accounts while meeting cyber insurance requirements.
Secure Wi-Fi 7
Next-gen Wi-Fi built for speed and security. Keep your office and remote users safe with WatchGuard’s advanced wireless protection.
Anti-Ransomware Protection
Stop ransomware before it spreads. Advanced detection and automated response to keep your data and business running.
Trusted by Clients & Partners
EXCELLENTTrustindex verifies that the original source of the review is Google. Varpath is my first call for anything in the field of infosec and cybersecurity, whether it's preparing for our SOC-2 audit, planning a pentest, or just checking keeping us up-to-date on the latest risks and vulnerabilities. I recommend them without reservation.Posted onTrustindex verifies that the original source of the review is Google. Varpath has been an excellent partner for our cybersecurity needs. They're professional, easy to communicate with, and do a great job safeguarding our data. Highly recommend for businesses wanting reliable protection!Posted onTrustindex verifies that the original source of the review is Google. Varpath is responsive, proactive, and explains security in simple language. They operate like a trusted security team, not just a vendor. Highly recommended for strong cybersecurity without complexity.Posted onTrustindex verifies that the original source of the review is Google. Varpath allows me to focus on my business and not the potential threats that can break it.Posted onTrustindex verifies that the original source of the review is Google. I reached out to Varpath last year to help with my laptop security. I was receiving so many links and emails due to my job and could not figure out who to trust. Then I clicked a bad link and ended up having a security breach with my information. After that, I became worried about doing anything with sensitive information on my computer. Now that Varpath makes sure that all my links and websites are safe, I’m able to work with zero stress and zero concern that I’m walking into something dangerous. It’s a lot like a weight has been lifted. I’m relatively tech savvy, but I’ve never understood what antivirus software actually works. Varpath makes sure to check in with me to see how the level of security is working and to make sure all my systems are still running seamlessly for me. I 100% recommend this company for device security.Posted onTrustindex verifies that the original source of the review is Google. I have worked with Jason (Varpath) for 20 plus years and I trust no one else with my internet security. He takes care of two of my businesses and when I open a second location for one of my businesses, he will take care of it too.